The very accessibility and ease of set up that’s made Google Apps the go-to service for email, collaboration, and cloud-based office tools also makes it a bit of a minefield when it comes to cloud security standards. As set up is so easy and straightforward, and you can even go from your starting point to having a working email and collaboration system in a few minutes, it’s possible that some of the more advanced Google Apps security features get overlooked. Google’s documentation doesn’t make things any better by not providing a step-by-step method. So in case you’re wondering how to get the optimum Google Apps security, here’s a quick guide.
Table of Contents
- Managing Google Apps security for your users
- Securing your organization’s email
- Google Drive security
Managing Google Apps security for your users
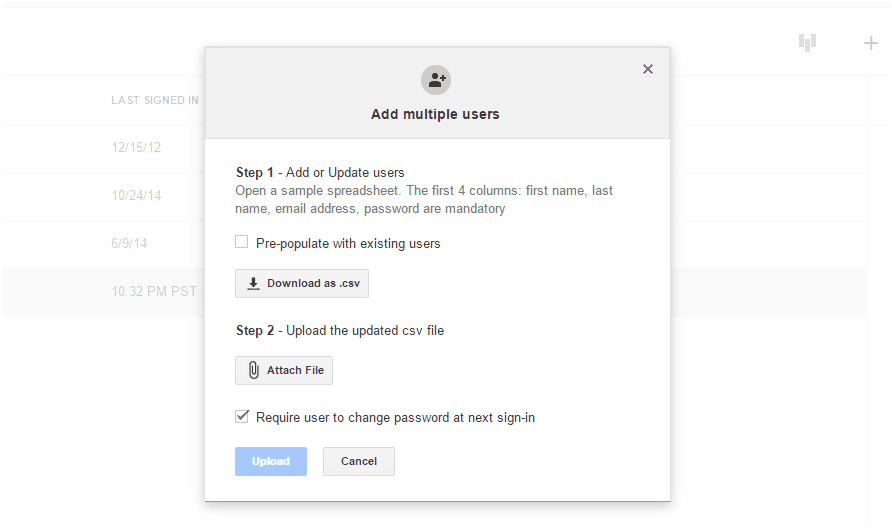
As administrator, adding users and assigning them to Organizational Units will be one of the first tasks you’ll encounter when setting up a Google Apps system at your workplace. Get this area right, and you’ll have it easier when you get down to setting up advanced Google Apps security for Gmail and Google Drive.
A. Applying policies to users
Setting up distinct Organizational Units and assigning users according to your company’s policies is one of the most critical tasks – as you’ll later in find yourself assigning security policies not directly to users, but to the OU they belong to. Here’s what all you need to keep in mind:
I. Assign users to the relevant OU: You can assign and move users around from the Users tab in the admin console. As Organizational Units make it easy to enable services and apply restrictions to users, your priority should be (in general) to create an OU hierarchy that will make it easier for you to give users just the right amount of access. Keep in mind that permissions are inherited – permissions and restrictions you place on an OU will trickle down to sub-units you create. It’s important to also follow vulnerability management practices, ensuring that inherited permissions do not introduce potential security risks at lower organizational levels.
II. Configure services: When you set up Google Apps for the first time, some services (like Gmail) will be enabled for all users. You can enable and disable services from the admin console. If you’ve assigned users to distinct Organizational Units, you can also enable and disable services on a per-OU basis. This comes in handy when you want to restrict specific users or departments from using services they do not need – for example, you could turn off Hangouts for some users, and Calendar for others.
III. Custom settings: While Google Apps security policies are inherited, you can also apply ‘local’ or custom settings. These will override inherited settings. For more on this, check out Google’s explanation: https://support.google.com/a/answer/4352075.
B. Password policies
Enforcing password policies is one of the best ways of securing any system as some users tend to choose passwords that are easily cracked or are found in publicly available password lists. However, do restrict the temptation to set very restrictive policies as that can have a rebound effect – of users writing down passwords! As a Google Apps administrator, you can force minimum length (found in Security > Basic settings), examine password strength and complexity (Security > Password monitoring), and set password recovery options.
NOTE: How to choose a strong password
Passwords have never been weaker. Thanks to improved computing power, the increased availability of password cracking tools, and of course, a spurt in industrial espionage and ‘cybercrime’, expect that your users will eventually be targeted. To stay safe, require your users to pick long character passwords (10 characters or more), with a mix of upper & lower case, numbers, and special characters. For more info on how to choose passwords, check out what Boston University and Carnegie Mellon University have to say on choosing a password.
C. 2-step verification
Few security measures are as effective as 2-factor authentication and we recommend this be used wherever available. Luckily, Google offers 2-factor authentication to Google apps users as well. You can enable this via the admin console (Security > Basic settings > 2-Step Verification > Allow users to turn on 2-factor authentication). When enabled, users will either have to enter a code sent through SMS or obtained via an approved authenticator app. You can also make this an overriding requirement to log on – but before that, do ensure that all your users have completed the end-user enrolment (found in their security settings panel).
D. Audit & logs
Apart from a security overview (Reports > Security) Google also offers the option of advanced auditing and logs, which might be especially useful or larger organizations:
I. Login audit log: Sooner or later, you can expect to become that target of an unauthorized entry attempt. The login audit log can help you keep track of these by logging all login attempts.
II. OAuth Token log: This helps administrators keep track of how third-party apps are accessing data of users within the organization.
III. Admin console audit log: This log keeps track of every action performed by an administrator. This comes in use when an organization has multiple administrators.
IV. Drive audit log: Google Drive Unlimited (a version meant for larger businesses) includes an audit & log functionality. Accessed via the admin console (Reports > Audit > Drive), the log contains information on item creation & access, containing parameters such as user name, IP address, ownership status…
V. Calendar audit log: The calendar audit log keeps track of changes to your users’ schedule and is useful in diagnosing any issues and scheduling problems
E. Set up alerts
It might also make sense at this stage to set up Google Apps’ alerting system to keep your informed of any Google Apps security beach or critical event. Found in your admin console (Reports > Manage Alerts) is a list of predefined alerts you can configure. For example, you can ask Google Apps to email you if there’s an app outage, or if another administrator changes Gmail settings or adds a new user.
Apart from these, you can also define custom alerts to keep you informed of events logged in the one of the audit logs Google offers (see Section 1.E above)
NOTE: Suspending and repairing compromised accounts
Even if you’ve set up the tightest possible Google Apps security for your organization’s Google Apps deployment, it’s possible that a user account gets compromised or a laptop gets stolen. In such an event, suspend the affected users (users > suspend> and reset their sign-in cookies to prevent anyone from logging in (Users > Account > Reset sign-in cookies)
Securing your organization’s email
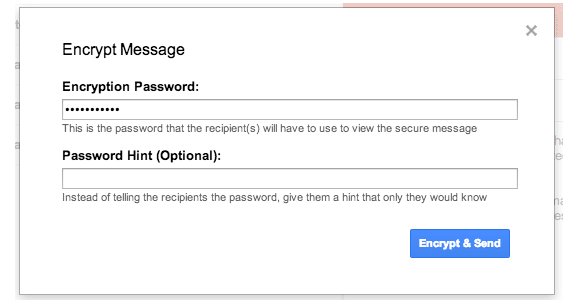
Email can be one of the biggest weaknesses in any organization’s security as it makes it easy for malware to sneak into your Mac or Windows device, and at the same time, enables inadvertent (or even deliberate) leaks of sensitive information and trade secrets. Here’s what you need to do if you’re concerned about this:
A. Whitelists & Blacklists
I. Whitelists: Email whitelists and blacklists can help your organisation combat the menace posed by spam and phishing attempts, while making sure that vital email doesn’t get marked as spam because some automated filter thought so. Found in the Google Apps Admin Console (Apps > Google Apps > Gmail > Advanced settings), the whitelists option lets you specify domains, individual IP addresses, or a range of addresses which you know are verified – for example, you might want to add your business’s branch offices and important vendors or clients to this list.
II. Blacklists: The Blocked Senders List, aka a blacklist, lets you specify rules that if triggered, will prevent inbound mail from reaching users in your organization. Found in the Google Apps Admin Console (Apps > Google Apps > Gmail > Advanced settings), the blocked senders option lets you specify addresses and domains you know are malicious or known for sending spam. This setting might come in use if spam or phishing attempts seem to be coming from specific domains or IP addresses (or a range of addresses).
B. Advanced settings for Gmail
Blacklists and whitelists are the most basic form of email filtering and Google Apps security. If you need advanced, more granular control over the mail users can send and receive, you’ll find the Advanced settings tab more useful (found in Apps > Google Apps > Gmail > Advanced Settings).
Gmail’s advanced settings include several options, including: adding footers to email, removing objectionable words and content, rules allowing or restricting attachments, restricting deliver to specific domains, addresses, or even your organization…
And, yes, as you’d expect, advanced settings are applied to organizational units and are inheritable – letting you specify varying levels of restrictions. For example, you might want your sales team to be allowed to send and receive mail without any restriction, and at the same time, require that personnel in your product development department only communicate with colleagues and approved vendors, and that too without being able to send attachments, or perhaps want to ensure that email containing sensitive keywords be routed to your legal team – all this is possible with Gmail’s Advanced settings option.
To read more about configuring advanced Gmail Settings, head over to https://support.google.com/a/answer/329608
C. Using DMARC, SPF and DKIM to prevent spammers from spoofing your email
Spam filters have improved so much that it’s almost guaranteed that most spam will get caught before it reaches someone’s inbox. That’s why spammers now try other tricks – like spoofing email accounts from domains known to be in good standing. So what happens if a spammer starts sending out emails that seem like they’ve come from your domain? Nothing good, that’s for sure – as it’s possible that some other domains start marking bonafide email from your company as spam – which can result in a lot of lost business. Here’s what you have to do to prevent this:
I. DKIM Authentication: DKIM authentication inserts a digital signature in outgoing mail, which tells other mails mail servers that the mail is from an authorized user, helping minimize the chance of email from your business being marked as spam by mistake. To set up DKIM, you’ll first have to generate a DKIM key (Apps > Google Apps > Gmail > Authenticate email), and then add this to a new TXT entry in your domain’s DNS records.
II. SPF Records: SPF records add another layer to making your email secure – they let other email servers know which all servers are authorized to send mail that appears to have come from your domain. This helps recipients ensure that mail from your servers is never marked as spam.
III. DMARC: DMARC is a way to telling other mail servers to reject mail that appears to have come from your domain but appears to be unauthenticated. This helps by making sure spammers can’t spoof your email addresses as any email they send will be unauthenticated, and will be rejected. Using a DMARC report tool can help you monitor and ensure that your policies are working effectively.
D. Encrypting your email
With recent disclosures of how governments around the world have been trying to gain access to email, your business might want to take steps to help safeguard its trade secrets. Sadly, Gmail doesn’t include any encryption options with Gmail, but it’s possible to rectify this using third-party Chrome extensions. Some of the popular ones include:
I. Secure email for Gmail: This Chrome plugin (www.streak.com/securegmail) from Streak requires that the sender and receiver decide upon a common password that will be used to decrypt the message. While it may not be the most elegant solution for widespread use, this tool might be handy if you only need to use encrypted email occasionally.
II. Mailvelope: Mailvelope (www.mailvelope.com) uses OpenPGP to encrypt your communications and works on Firefox and Chrome. You’ll need to set up a private key and a password to encrypt and decrypt messages.
Google Drive security
Seamless integration with Gmail has made Google Drive the new king of cloud storage and collaboration suites. But if Gmail security remains obscure, Google Drive security is even more so. But Google does give you many options to help ensure you’re safeguarding your documents and online data as well as possible.
A. Restricting sharing & access
More often than not, your employees will be collaborating on documents within the company itself. With Google Apps, you can specify, and restrict access to who all documents can be shared with – outside the organization, or even within. You’ll find the Google Drive security options within your admin console (Apps > Google Apps > Drive > Sharing settings). Options include setting sharing options on a per-user or per-Organizational Unit basis, allowing users to work on documents shared with them from outside your organisation. Also, as administrator, you can create work folders for each department and Organizational Unit, giving access to users as required.
You can also use the admin console to transfer ownership of documents from one user to another if required – for example, if an employee gets transferred to another project or leaves the company.
B. Restricting apps
One of the things that makes Google Drive so useful is the amount of apps that can be used alongside – from CRM apps to collaboration and calendaring tools. But sometimes you might want to restrict certain apps, or even prevent critical data from being accessed by third-party apps. You’ll find this option in your account dashboard (Authorizingapplications & sites). From here, you can remove applications you no longer use or no longer trust with your data.
C. Encrypting your Google Drive files
As with Gmail, Google Drive doesn’t include any in-built way of encrypting your files and documents, and you’ll have to turn to a third-party service to do so:
I. Boxcryptor: With mobile as well as desktop apps, Boxcryptor (www.boxcryptor.com) uses AES-256 and RSA encryption to encrypt files on your device before uploading them to Google Drive.
II. Fogpad: Fogpad (www.fogpad.com) is a web app that uses client-side AES-256 encryption to create secure text documents.
III. Seclore FileSecure: This cloud-based Information Rights Management service (www.seclore.com) can secure up to 64 kinds of file formats and provides administrators features like file usage tracking and audit, secure file sharing, and automatic expiration of access.
D. Backup options for Google Apps
While Google’s expertise might seem to be enough to guarantee the safety of your data, a backup plan is essential to guard against data loss or corruption. After all, viruses, malware, hardware failures, human error… the list of things that can go wrong is rather lengthy.
I. Google Apps Vault: Users of Google Apps unlimited get free access to the Vault add-on, which provides extensive backup and eDiscovery services. Features include email archiving, legal hold on documents, advanced search, export of mail and documents… Other Google Apps subscribers can also utilise this service, but for a fee.
II. Backupify: One of the more popular third-party services for Google Apps backup, Backupify can safeguard from data loss – across Google Mail, Google Drive, Contacts, Calendar, and Sites. Features include multiple backups each day, HIPAA compliance, encryption, and monitoring and audit logging.
We hope this quick guide to Google Apps security can get you started on building a more robust IT environment for your business or non-profit. While this is an only an overview, it captures most of the common options offered by Google, along with third-party apps that fill in the gaps. Stay tuned to our blog for more on small business IT, productivity, and collaboration tips and guides.
 Skip to content
Skip to content